Fortigate | High Availability
Berikut Konfigurasi untuk masing Forti (FG-Primary dan FG-Secondary)
config system global
config system global
set hostname FGT-Primary
set timezone 53
end
config system interface
edit port1
set mode static
set ip 192.168.101.1/24
set allowaccess ping
set role wan
set alias Internet1
next
edit port2
set ip 192.168.102.1/24
set allowaccess ping
set role wan
set alias Internet2
next
edit port3
set ip 10.0.1.254/24
set allowaccess ping http https ssh
set role lan
set alias LAN
next
edit port4
set ip 10.1.0.254/24
set role dmz
set alias DMZ
next
edit port5
set ip 192.168.230.254/24
set allowaccess ping http fgfm ssh https
set role wan
set alias MGMT
next
end
config system dns
set primary 8.8.8.8
set secondary 8.8.4.4
end
config system sdwan
set status enable
config members
edit 1
set interface port1
set gateway 192.168.101.254
next
edit 2
set interface port2
set gateway 192.168.102.254
next
end
config system sdwan
config health-check
edit Default_DNS
set members 1 2
next
end
end
config router static
edit 1
set sdwan enable
end
config firewall address
edit 10.0.1.0/24-LAN
set subnet 10.0.1.0/24
next
edit 10.1.0.0/24-DMZ
set subnet 10.1.0.0/24
end
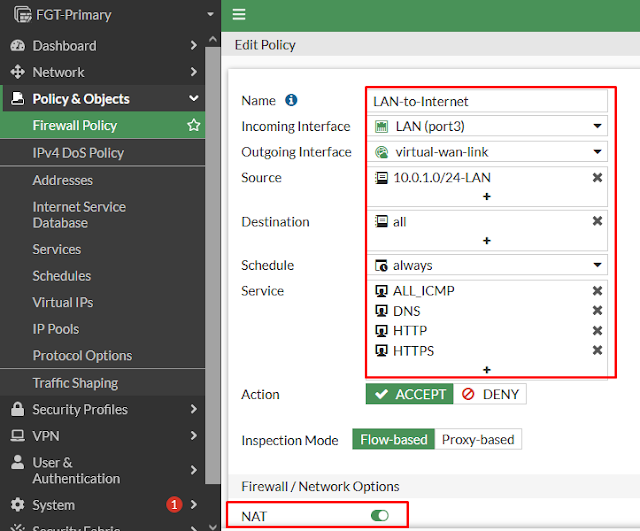
config firewall policy
edit 1
set srcintf port3
set dstintf virtual-wan-link
set srcaddr 10.0.1.0/24-LAN
set dstaddr all
set schedule always
set service ALL_ICMP HTTP HTTPS DNS
set action accept
set name LAN-to-Internet
set logtraffic all
set nat enable
next
edit 2
set srcintf port4
set dstint virtual-wan-link
set srcaddr 10.1.0.0/24-DMZ
set dstaddr all
set schedule always
set service ALL_ICMP HTTP HTTPS DNS
set action accept
set name DMZ-to-Internet
set logtraffic all
set nat enable
next
edit 3
set srcintf port3
set dstintf port4
set srcaddr 10.0.1.0/24-LAN
set dstaddr 10.1.0.0/24-DMZ
set schedule always
set service ALL
set action accept
set logtraffic all
set name LAN-to-DMZ
next
end
-----------------------------------------------
Tahap-2
Setting IP Management FGT-Secondary
FGT-Secondary IP Management dengan IP address 10.0.1.253/24 pada port3, seperti pada berikut ini.
config system global
set hostname FGT-Seconday
set timezone 53
end
config system interface
edit port3
set mode static
set ip 10.0.1.253/24
set allowaccess ping http fgfm ssh https
next
config system interface
edit port5
set ip 192.168.230.253/24
set allowaccess ping http fgfm ssh https
set role wan
set alias MGMT
next
end
Lanjut Konfig SDWAN
Lanjut Static Route
Firewall Policy (LAN to internet, DMZ to Internet, dan LAN toMZ)

Verifiaski, Memastikan sdh syncron
Triger, cb restart FG-Primary, dan lakukan ping 8.8.8.8 paly youtube dari user-LAN, apakah ada downtime.
Observer HA Failover Menggunakan Diagnostic commands
Pada FGT-Primary, login sebagai admin, kemudian ketik
perintah berikut ini.
#diagnosa debug enable
Untuk memberhentikan debug, ketik perintah 🡪
#diagnose debug application hatalk 0
Configuring HA Management Interface. Mengakses FGT-Secondary dari FGT-Primary. Dari FGT-Primary masuk ke console, menggunakan perintah berikut ini untuk mengakses FGT-Secondary, ketik perintah 🡪 exe ha manage 0 admin
Kemudian masukkan password –nya.
Set Up Management Interface
Pada User-LAN
mengakses FGT-Primary, masuk ke System
> HA, klik kanan pada
FGT-Primary, klik Edit seperti
gambar di bawah ini.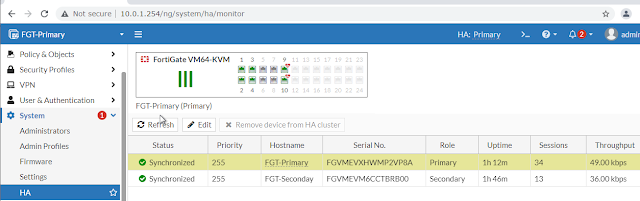

Lanjut: Config IP port 7 untuk management pd FG-Primary
config system interface
edit port7
set ip 10.0.1.252/24
set allowaccess ping http https ssh fgfm
set role lan
set alias LAN
next
end
Dari User-LAN, akses FortiGate ke alamat http://10.0.1.252
Konfigurasi dan Mengakses FGT-Secondary Menggunakan Management Interface.
Masuk ke FGT-Secondary, masuk sebagai admin, ketik perintah
🡪 show system ha,
seperti pada gambar di bawah ini.
Kemudian dari User-LAN, menggunakan browser mengakses
FGT-Secondary http://10.0.1.253.
Sehingga untuk FGT-Primary dan FGT-Secondary masing-masing mempunyai IP Management pada interface port7.
Melepas FortiGate dari HA
Dari User-LAN, masuk ke FGT-Primary http://10.0.1.254, dengan username admin, masuk ke System > HA, klik pada FGT-Secondary, kemudian klik Remove device from HA Cluster.



























Posting Komentar untuk "Fortigate | High Availability"