PaloAlto | High Availability (HA)
Lab kali ini kita akan buat simulasi High Availability (HA) pada
firewall, tujuannya adalah membuat redudancy firewall palo, dimana ketika
salah satu firewall down, maka ada firewall backup, atau ketika salah
jalur link ke atao dari firewall mati, maka akan ada jalur lain yg
bisa dilewati dari segment serverfarm ke outside (area internet)
atau dari sebaliknya. Langsung sj, lihat topologi dibawah ini.
Masing-masing router kita konfigurasi terlebih dahulu>
Router R1
hostname R-INET-01
!
interface GigabitEthernet0/0
description LINK-TO-FW-T1-01
ip address 202.191.100.2 255.255.255.248
ip nat inside
standby 1 ip 202.191.100.1
standby 1 priority 110
standby 1 preempt
standby 1 track 1 decrement 20
ip ospf network point-to-point
ip ospf 1 area 0
!
interface GigabitEthernet0/1
ip address 192.168.14.111 255.255.255.0
ip nat outside
no shut
!
interface GigabitEthernet0/2
description LINK-to-R-INET-02
ip address 11.11.11.253 255.255.255.252
ip ospf network point-to-point
ip ospf 1 area 0
no shut
!
router ospf 1
redistribute static subnets
default-information originate
!
access-list 1 permit any
!
ip nat inside source list 1 interface GigabitEthernet0/1 overload
ip route 0.0.0.0 0.0.0.0 192.168.14.2
!track 1 ip route 8.8.8.8 255.255.255.255 reachability
!
R-INET-01#
!
interface GigabitEthernet0/0
description LINK-TO-FW-T1-01
ip address 202.191.100.2 255.255.255.248
ip nat inside
standby 1 ip 202.191.100.1
standby 1 priority 110
standby 1 preempt
standby 1 track 1 decrement 20
ip ospf network point-to-point
ip ospf 1 area 0
!
interface GigabitEthernet0/1
ip address 192.168.14.111 255.255.255.0
ip nat outside
no shut
!
interface GigabitEthernet0/2
description LINK-to-R-INET-02
ip address 11.11.11.253 255.255.255.252
ip ospf network point-to-point
ip ospf 1 area 0
no shut
!
router ospf 1
redistribute static subnets
default-information originate
!
access-list 1 permit any
!
ip nat inside source list 1 interface GigabitEthernet0/1 overload
ip route 0.0.0.0 0.0.0.0 192.168.14.2
!track 1 ip route 8.8.8.8 255.255.255.255 reachability
!
R-INET-01#
Router R2
hostname R-INET-02
!
interface GigabitEthernet0/0
description LINK-TO-FW-T1-01
ip address 202.191.100.3 255.255.255.248
ip nat inside
standby 1 ip 202.191.100.1
standby 1 preempt
ip ospf network point-to-point
ip ospf 1 area 0
!
interface GigabitEthernet0/1
ip address 10.0.137.112 255.255.255.0
ip nat outside
no shut
!
interface GigabitEthernet0/2
description LINK-to-R-INET-02
ip address 11.11.11.254 255.255.255.252
ip ospf network point-to-point
ip ospf 1 area 0
no shut
!
router ospf 1
redistribute static subnets
default-information originate
!
access-list 1 permit any
!
ip nat inside source list 1 interface GigabitEthernet0/1 overload
ip route 0.0.0.0 0.0.0.0 10.0.137.1
!
R-INET-02#
hostname R-INET-02
!
interface GigabitEthernet0/0
description LINK-TO-FW-T1-01
ip address 202.191.100.3 255.255.255.248
ip nat inside
standby 1 ip 202.191.100.1
standby 1 preempt
ip ospf network point-to-point
ip ospf 1 area 0
!
interface GigabitEthernet0/1
ip address 10.0.137.112 255.255.255.0
ip nat outside
no shut
!
interface GigabitEthernet0/2
description LINK-to-R-INET-02
ip address 11.11.11.254 255.255.255.252
ip ospf network point-to-point
ip ospf 1 area 0
no shut
!
router ospf 1
redistribute static subnets
default-information originate
!
access-list 1 permit any
!
ip nat inside source list 1 interface GigabitEthernet0/1 overload
ip route 0.0.0.0 0.0.0.0 10.0.137.1
!
R-INET-02#
Switch-INET
hostname SW-INET-01
!
no cdp run
!
vlan 10
!
interface vlan 10
no shut
ip address 192.168.255.254 255.255.255.0
ip ospf 1 area 0
interface GigabitEthernet0/0
switchport access vlan 10
switchport mode access
negotiation auto
!
interface GigabitEthernet0/1
switchport access vlan 10
switchport mode access
negotiation auto
!
interface GigabitEthernet0/2
switchport access vlan 10
switchport mode access
negotiation auto
!
interface GigabitEthernet0/3
switchport access vlan 10
switchport mode access
negotiation auto
!
Switch ServerFarm
hostname SW-SF-01
!
interface Loopback1
ip address 192.168.255.2 255.255.255.255
ip ospf 1 area 0
!
interface GigabitEthernet0/0
description LINK-TO-PALOALTO
switchport access vlan 254
negotiation auto
!
interface GigabitEthernet0/1
description LINK-TO-PALOALTO
switchport access vlan 254
negotiation auto
!
interface GigabitEthernet0/2
switchport access vlan 10
switchport mode access
negotiation auto
!
interface Vlan10
ip address 10.87.10.253 255.255.255.0
standby 1 ip 10.87.10.1
standby 1 priority 110
standby 1 preempt
ip ospf 1 area 0
!
interface Vlan254
description LINK-TO-FW-T1-01
ip address 10.90.10.252 255.255.255.248
standby 1 ip 10.90.10.253
standby 1 priority 110
standby 1 preempt
ip ospf 1 area 0
!
router ospf 1
default-information originate
!
ip route 0.0.0.0 0.0.0.0 10.90.10.254
!
hostname SW-INET-01
!
no cdp run
!
vlan 10
!
interface vlan 10
no shut
ip address 192.168.255.254 255.255.255.0
ip ospf 1 area 0
interface GigabitEthernet0/0
switchport access vlan 10
switchport mode access
negotiation auto
!
interface GigabitEthernet0/1
switchport access vlan 10
switchport mode access
negotiation auto
!
interface GigabitEthernet0/2
switchport access vlan 10
switchport mode access
negotiation auto
!
interface GigabitEthernet0/3
switchport access vlan 10
switchport mode access
negotiation auto
!
Switch ServerFarm
hostname SW-SF-01
!
interface Loopback1
ip address 192.168.255.2 255.255.255.255
ip ospf 1 area 0
!
interface GigabitEthernet0/0
description LINK-TO-PALOALTO
switchport access vlan 254
negotiation auto
!
interface GigabitEthernet0/1
description LINK-TO-PALOALTO
switchport access vlan 254
negotiation auto
!
interface GigabitEthernet0/2
switchport access vlan 10
switchport mode access
negotiation auto
!
interface Vlan10
ip address 10.87.10.253 255.255.255.0
standby 1 ip 10.87.10.1
standby 1 priority 110
standby 1 preempt
ip ospf 1 area 0
!
interface Vlan254
description LINK-TO-FW-T1-01
ip address 10.90.10.252 255.255.255.248
standby 1 ip 10.90.10.253
standby 1 priority 110
standby 1 preempt
ip ospf 1 area 0
!
router ospf 1
default-information originate
!
ip route 0.0.0.0 0.0.0.0 10.90.10.254
!
Seting Firewall Palo Alto
Sebelum kita masuk kebagian seting HA, terlebih dahulu kita seting IP Management dimasing-masing firewall, baik firewall active dan passice.
Sebelum kita masuk kebagian seting HA, terlebih dahulu kita seting IP Management dimasing-masing firewall, baik firewall active dan passice.
Lalu kita masuk bagian seting HA, mode yg kita pilih adalah Active-Passive. Device --> High Availability --> General
Device --> High Availability --> HA-Communication
Device --> High Availability --> Link and Path Monitor
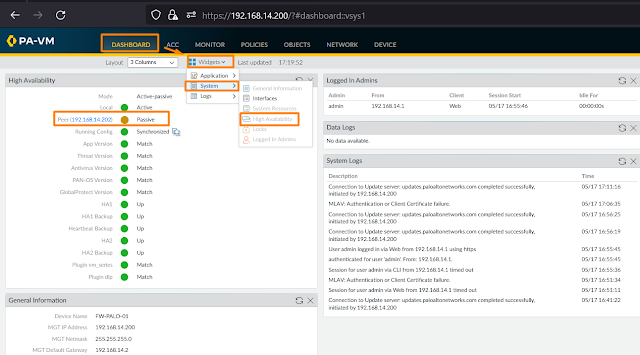
Jika HA nya sudah berhasil, nampak seperti screenshot dibawah ini, Firewall Primary (Active)
Selanjutnya masuk dibgian seting interface IP, routing, DNS, hostname, policy rules, NAT dl.
Catan: Jika firewall primary ato secondari transisi dari mode active ke passive atau sebaliknya, untuk mengkatifkan kembali bs dilakukan dengan cara mode opration. Misal muncul seperti gambar dibawah.
Action yg dilakukan untuk solve kembali adalah
---------------------------------------------
palo alto










Posting Komentar untuk "PaloAlto | High Availability (HA)"